

One of the main functions of guard tour patrol systems is collecting patrol checkpoint data. This refers to specific locations or points on a patrol route where security officers must check-in or act, such as scanning a tag, pressing a button, or reading data. These checkpoints are strategically placed throughout the venue and designed to ensure that security officers follow the designated route and do not miss any areas.
Patrol checkpoint data is typically recorded in real-time and may include information such as the exact time the officer arrived at the checkpoint, GPS location, and any events or actions that occurred during the check. By collecting this data, security managers can track whether patrols are completed correctly and on time. This data also provides valuable insights into patrol frequency, potential gaps, and areas needing additional attention.
Officer activity data collected by guard tour patrol systems ensures that security personnel perform their duties efficiently. This data can include information about actions taken by officers during a patrol, such as checking doors, windows, or security equipment. The system can track the activities officers perform in real-time, including the time spent at each location and any anomalies or irregularities discovered during the patrol.
For example, suppose a guard spends an unusually long time at a particular location. This may indicate a need for a more detailed inspection or alert the security team to a potential problem. Activity data also helps evaluate the effectiveness of patrol plans and the workload distribution across the security team.
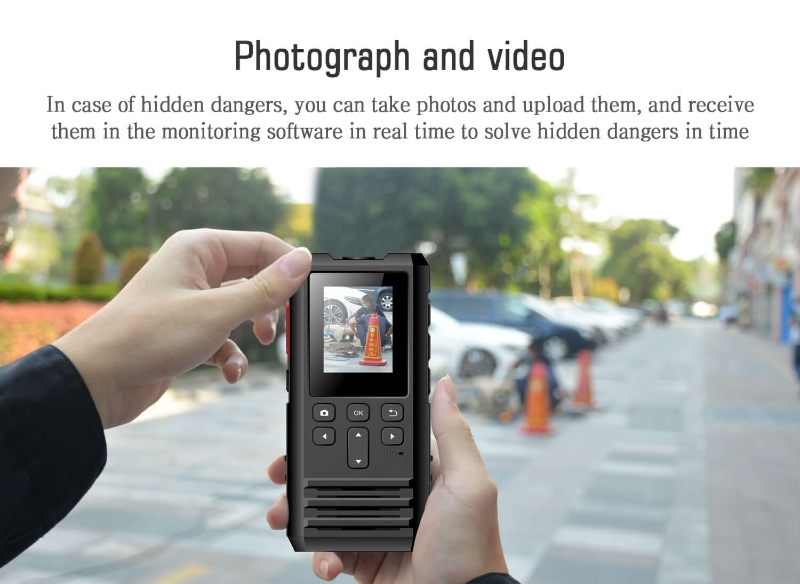
An essential feature of any guard tour patrol system is the ability to collect incident data. This includes any unusual events or incidents during a patrol, such as security breaches, equipment failures, or environmental hazards. The system typically prompts the guard to record specific details of the incident, such as the type of incident, where the incident occurred, when the incident occurred, and any response actions taken. Incident data is essential to security management because it provides an organized and detailed record of any security-related incident. By collecting this data, security teams can quickly respond to emergencies, evaluate patterns of recurring problems, and develop preventive strategies.
Time and date stamps are among the most critical data types that patrol systems collect. The system records the exact time and date of each action, checkpoint visit, or event. This data proves that security personnel conduct patrols as planned and use it to verify that guards adhere to their assigned shifts. Time and date stamps also provide transparency and traceability, as they help ensure that officers perform their duties within the required time. These timestamps are particularly useful when reviewing security operations, as they allow management to track delays, monitor efficiency, and analyze discrepancies in patrol data. They are also essential for generating detailed reports and auditing security activities, helping organizations comply with internal and external security regulations.

Another key type of data that patrol systems collect is GPS and location data. This enables security managers to track the precise location of guards during patrols. GPS tracking ensures that guards follow the correct route and visit designated checkpoints at the right time.
By collecting GPS and location data, the system helps improve patrol operations' overall efficiency and safety. If a guard strays from a designated route or fails to reach a specific checkpoint, security managers can immediately identify and address the problem. Additionally, location data is instrumental in emergencies, as it can pinpoint where security personnel are and provide assistance when needed.
Collecting data provides a comprehensive view of security operations, ensuring that every aspect of the patrol process is monitored and optimized. From checkpoint visits and officer activity to incidents and environmental conditions, the data collected is invaluable for improving security management, ensuring compliance, and increasing operational efficiency. By leveraging the rich data provided by modern patrol systems, security teams can take proactive security measures, resolve issues before they escalate, and improve the overall safety of a venue.